Difference between revisions of "Windows netsh networking"
| Line 56: | Line 56: | ||
;ICMP rules | ;ICMP rules | ||
<syntaxhighlightjs lang=powershell> | <syntaxhighlightjs lang=powershell> | ||
netsh advfirewall firewall add rule name="ICMP allow ingress ipv4 echo-requests" protocol=icmpv4:8,any dir=in action=allow #or block | |||
netsh advfirewall firewall delete rule name="ICMP allow ingress ipv4 echo-requests" protocol=icmpv4:8,any dir=in | |||
netsh firewall set icmpsetting 8 enable #or disable | netsh firewall set icmpsetting 8 enable #or disable | ||
netsh advfirewall firewall add rule name="All ICMP V4" protocol=icmpv4:any,any dir=in action=allow | |||
netsh firewall set icmpsetting type=ALL mode=enable | netsh firewall set icmpsetting type=ALL mode=enable | ||
netsh advfirewall firewall add rule name="Block Type 13 ICMP V4" protocol=icmpv4:13,any dir=in action=block | |||
netsh firewall set icmpsetting 13 disable all | netsh firewall set icmpsetting 13 disable all | ||
</syntaxhighlightjs> | </syntaxhighlightjs> | ||
Latest revision as of 20:46, 10 January 2019
Examples of use of netsh.exe Windows command-line utility to manipulate local or remote machine network configuration
List IPv4 and IPv6 addresses
It gives nicer output than ipconfig
netsh interface ip show addresses netsh interface ipv6 show addresses
Set IPv4 address
netsh interface ip set address "Ethernet" static hostipaddre 255.255.255.0 hostgatewayaddress netsh interface ip set address "Ethernet" static 10.50.10.41 255.255.255.0 10.50.41.1
Set IPv6 address
Configure interface with ipv6 address, interface name "Local Area Connection"
netsh interface ipv6 set address "Local Area Connection" 2001:db8:acad:1::3
Import wireless profile
- Export profile
Netsh wlan export profile folder= PathAndFileName [[name=] ProfileName] [[interface=] InterfaceName] [[key=] clear] Netsh wlan export profile folder=%USERPROFILE%\Downloads\Wifiprofiles name=Guest_wireless interface="Wireless Network Connection"
- Import profile
Netsh wlan add profile filename= PathAndFileName [[interface=]InterfaceName] [[user=]{all|current}]
Netsh wlan add profile filename="Wireless Network Connection-Guest_wireless.xml" interface="Wireless Network Connection" user=all
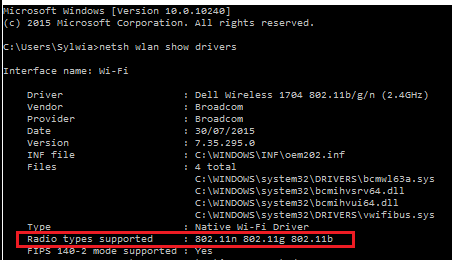
Check wireless card band capability - 2.4Ghz or 5Ghz
OS: Windows 7, not recognized on W2012R2 Data Center
netsh wlan show drivers
- If the network adapter supports network modes 802.11g and 802.11n:
- The computer has 2.4 GHz network capability ONLY & IS NOT Dual-Band Capable.
- If the network adapter supports network modes 802.11a and 802.11g and 802.11ac and 802.11n:
- The computer has 2.4 GHz and 5GHz network capability IS Dual-Band Compable.
- The network adapter supports network modes 802.11n and 802.11g and 802.11b:
- The computer has 2.4GHz network capability ONLY & IS NOT Dual-Band Capable.
Firewall
netsh firewall command has been deprecated in Windows Server 2012 in favour of a new command netsh advfirewall firewall.
<syntaxhighlightjs lang=powershell>
- Add new rule
netsh advfirewall firewall add rule name="Open port :80" dir=in action=allow protocol=TCP localport=80
- Show all rules
netsh advfirewall firewall show rule name=all
- Enable/disable firewall
netsh advfirewall set allprofiles state on
- Reset a firewall to defaults
netsh advfirewall reset
- Change FW default log file from c:\Windows\system32\LogFiles\Firewall\pfirewall.log to c:\temp directory
netsh advfirewall set currentprofile logging filename "C:\temp\pfirewall.log"
- Export / import FW settings
netsh advfirewall export "C:\temp\WFconfiguration.wfw" </syntaxhighlightjs>
- ICMP rules
<syntaxhighlightjs lang=powershell> netsh advfirewall firewall add rule name="ICMP allow ingress ipv4 echo-requests" protocol=icmpv4:8,any dir=in action=allow #or block netsh advfirewall firewall delete rule name="ICMP allow ingress ipv4 echo-requests" protocol=icmpv4:8,any dir=in netsh firewall set icmpsetting 8 enable #or disable
netsh advfirewall firewall add rule name="All ICMP V4" protocol=icmpv4:any,any dir=in action=allow netsh firewall set icmpsetting type=ALL mode=enable
netsh advfirewall firewall add rule name="Block Type 13 ICMP V4" protocol=icmpv4:13,any dir=in action=block netsh firewall set icmpsetting 13 disable all </syntaxhighlightjs>
Tracing
OS: Windows 7, Windows Server 2008 and newer
netsh trace help netsh trace show capturefilterhelp #capture filter examples netsh trace show status IPConfig /FlushDNS #clear DNS name cache NBTStat -R #clear NetBIOS name cache #Capture all traffic using NetConnection scenario, network connection diagnostics Netsh trace start scenario=NetConnection capture=yes report=yes persistent=no maxsize=2024 correlation=yes traceFile=C:\Logs\NetTrace.etl netsh trace stop
- Capture from a IP interface
netsh trace start scenario=NetConnection capture=yes report=yes persistent=no maxsize=2024 correlation=yes traceFile=C:\Logs\NetTrace.etl Ethernet.Type=IPv4 IPv4.Address=192.168.1.142 netsh trace start capture=yes Ethernet.Type=IPv4 IPv4.Address=192.168.1.142 traceFile=C:\Logs\NetTrace2.etl
Start Powershell script to capture that only contains traffic between the local system and two remote IP addresses (10.0.2.1 and 10.0.3.1). Note the Local IP address is found using Get-NetIPAddress and looking for a NIC named *Virtual*. Use route print -4 to list interfaces name.
$filename = "c:\logs\${env:computername}_netsh_trace.etl"
$IPs = "({0},10.0.2.1,10.0.3.1)" -f (Get-NetIPAddress -AddressFamily IPv4 -InterfaceAlias *Virtual*).IPAddress
netsh trace start capture=yes tracefile=$filename maxsize=2048 filemode=circular overwrite=yes report=no correlation=no IPv4.SourceAddress=$IPs IPv4.DestinationAddress=$IPs Ethernet.Type=IPv4
Analysing
Install Microsoft's Message Analyzer app that can read ETL format http://www.microsoft.com/en-us/download/details.aspx?id=44226
Convert ETL to PCAP using a PowerShell script (not tested) or use save as... in Message Analiser
$s = New-PefTraceSession -Path “C:\output\path\spec\OutFile.Cap” -SaveOnStop $s | Add-PefMessageProvider -Provider “C:\input\path\spec\Input.etl” $s | Start-PefTraceSession
References
- Netsh tracing isc.sans.edu
- Network tracing (packet sniffing) built-in to Windows Clients (7,8,8.1,10) and Windows Server (2008 R2, 2012, 2012 R2