AWS/S3 Bucket Policies
S3 bucket policies
Secure S3 bucket and objects using S3 bucket policies, which are written as JSON documents and attached to the bucket we are securing
- S3 policies are resource-based policies as are attached to a resource eg. S3
- IAM policies in contrast are indentity-based policies are attached to an entity(identity) eg. IAM user, group or role that are making API call
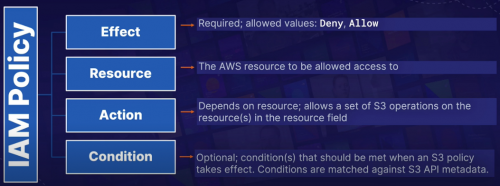
Logic:
- if IAM policy or S3 bucket policy allows then access is allowed, an explicit deny in any overrides the allow
Note: In an IAM policy, there is no Principal field, as it is already implied to be a IAM user, group or role; therefore there's no need to specify.
Working with JSON
Download Notepad++ plugin nppjsonviewer. Install the plugin by just dropping the DLL in the plugin folder. You can also use Plugin Manager bu going to Plugins > Plugin Manager > Show Plugin Manager > find JSON Viewer last current version 1.21.
Plugin shows the JSON in a tree format in a separate frame, it also formats JSON in a readable format in the main Notepad++ window. To format a JSON string, paste it into Notepad++ and select it. Then go to Plugins > JSON Viewer > Format JSON [Ctrl+Alt+Shift+M] and it should instantly format it for you, then choose Show JSON Viewer [Ctrl+Alt+Shift+J]
Block Public Access Feature
Public meaning in respect to S3 ACLs:
- A bucket or object is public if it grants access to the members of predefined groups:
AllUsersorAuthenticatedUsers(these are any AWS logged in user)
in respect to S3 policies:
- an S3 policy that allows public access are when wildcard is in use, or cross-account access policies
Non-public means policy doesn't use wildcards for entities like VPCs, users, accounts, then the Block Public Access does not have any affect.
Read-only access to certain S3 buckets
A sample AWS IAM json policy file with read-only access to certain S3 buckets. Formatted by JSON Viewer in NP++
{
"Statement": [{
"Effect": "Allow",
"Action": ["s3:ListBucket",
"s3:GetObject",
"s3:GetObjectVersion"],
"Resource": ["arn:aws:s3:::my_bucket/*",
"arn:aws:s3:::my_bucket"]
}],
"Statement": [{
"Effect": "Allow",
"Action": ["s3:ListBucket",
"s3:GetObject",
"s3:GetObjectVersion"],
"Resource": ["arn:aws:s3:::my_other_bucket/*",
"arn:aws:s3:::my_other_bucket"]
}],
"Statement": [{
"Effect": "Allow",
"Action": ["s3:ListAllMyBuckets"],
"Resource": "*",
"Condition": {
}
}]
}
Limited access to users named buckets
This policy structure can be used in a scenario you have someone to administrate a group of clients to that can upload their files that are too big for an email to be send to you. In this case you can create following three groups where users in bucketsadmins group have full access to a company AWS account and can create a user, add, remove, create access keys for your clients. Then these clients need to be placed in bucketusers to lock them down only to one bucket where they have only API access.
- admins - full account administration access to a console and API
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
- bucketsadmins -these users have a full console & API user management access on bucketusers group and full access to S3 within AWS account
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowUsersToPerformUserActions",
"Effect": "Allow",
"Action": [
"iam:*User",
"iam:ListUsers",
"iam:ListGroups",
"iam:*UserPolicy",
"iam:ListGroupsForUser",
"iam:ListUserPolicies",
"iam:*LoginProfile",
"iam:*AccessKey*",
"iam:*SigningCertificate*",
"iam:*MFADevice*"
],
"Resource": [
"arn:aws:iam::account-id-without-hyphens:user/*",
"arn:aws:iam::account-id-without-hyphens:group/*"
]
},
{
"Sid": "AllowUsersToAddAndDeleteUserFromGroup",
"Effect": "Allow",
"Action": [
"iam:RemoveUserFromGroup",
"iam:AddUserToGroup"
],
"Resource": [
"arn:aws:iam::account-id-without-hyphens:group/bucketusers"
]
},
{
"Sid": "AllowUsersToSeeStatsOnIAMConsoleDashboard",
"Effect": "Allow",
"Action": [
"iam:GetAccount*",
"iam:ListAccount*"
],
"Resource": [
"*"
]
},
{
"Sid": "S3FullAccess",
"Effect": "Allow",
"Action": "s3:*",
"Resource": "*"
}
]
}
- bucketusers -users have full API access to their buckets named xyzcompany-awsusername
{
"Version": "2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Action":[
"s3:ListAllMyBuckets"
],
"Resource":"arn:aws:s3:::*"
},
{
"Effect":"Allow",
"Action":[
"s3:ListBucket",
"s3:GetBucketLocation"
],
"Resource":"arn:aws:s3:::xyzcompany-${aws:username}"
},
{
"Effect":"Allow",
"Action":[
"s3:PutObject",
"s3:GetObject",
"s3:DeleteObject"
],
"Resource":"arn:aws:s3:::xyzcompany-${aws:username}/*"
}
]
}