Difference between revisions of "Wireshark and Tshark"
Jump to navigation
Jump to search
| (One intermediate revision by the same user not shown) | |||
| Line 3: | Line 3: | ||
Prerequisites - Allow root SSH on Ubuntu | Prerequisites - Allow root SSH on Ubuntu | ||
Edit <tt>/etc/ssh/sshd_config</tt> to allow root password logins through ssh. As shown below, comment out #PermitRootLogin without-password and add PermitRootLogin yes. | Edit <tt>/etc/ssh/sshd_config</tt> to allow root password logins through ssh. As shown below, comment out #PermitRootLogin without-password and add PermitRootLogin yes. | ||
<source lang=bash> | |||
# Authentication: | |||
LoginGraceTime 120 | |||
#PermitRootLogin without-password | |||
PermitRootLogin yes | |||
</source> | |||
Create named pipe on a system A where Wireshark is installed | Create named pipe on a system A where Wireshark is installed | ||
<source lang=bash> | |||
sudo mkfifo /tmp/remote | |||
</source> | |||
Read from the pipe on system A to Wireshark | Read from the pipe on system A to Wireshark | ||
<source lang=bash> | |||
sudo wireshark -k -i /tmp/remote | |||
</source> | |||
Connect to system B as root user to a remote node then redirect tcpdump output to the named pipe over ssh to system A | Connect to system B as root user to a remote node then redirect tcpdump output to the named pipe over ssh to system A | ||
<source lang=bash> | |||
ssh root@monior-this-host.com "tcpdump -s 0 -U -n -w - -i eth0 not port 22" > /tmp/remote | |||
</source> | |||
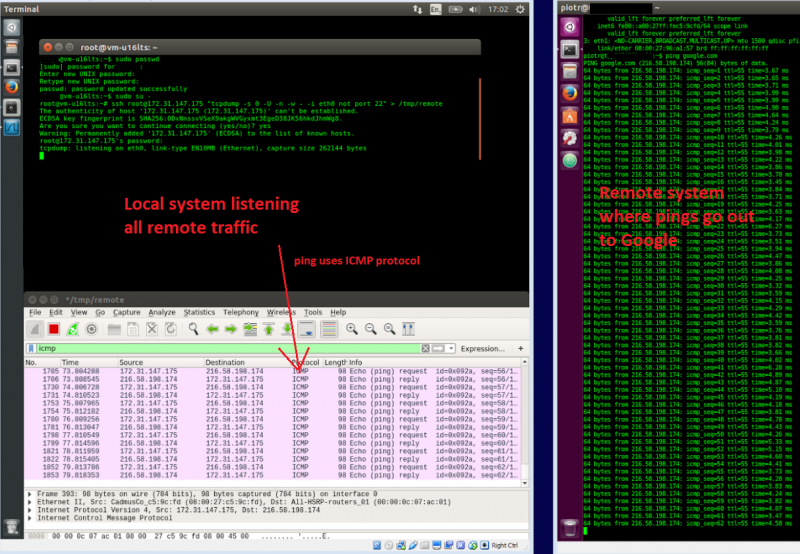
[[File:Wireshark-named-pipe.PNG|none|800px|left|Wireshark-named-pipe]] | [[File:Wireshark-named-pipe.PNG|none|800px|left|Wireshark-named-pipe]] | ||
| Line 21: | Line 33: | ||
= Filters = | = Filters = | ||
Operators | Operators | ||
<source lang=bash> | |||
! - no, && - and, || - or | |||
</source> | |||
No STP, No Arp, No ipv6, no nbns, no DHCP | No STP, No Arp, No ipv6, no nbns, no DHCP | ||
<source lang=bash> | |||
!stp && !arp && !ipv6 && !dhcpv6 && !nbns && !bootp.option.type == 53 | |||
</source> | |||
= Allow non-root (current) user to run tcpdump = | |||
<source lang=bash> | |||
#!/usr/bin/env bash | |||
# NOTE: This will let anyone who belongs to the 'pcap' group | |||
# execute 'tcpdump' | |||
# NOTE2: User running the script MUST be a sudoer. It is | |||
# convenient to be able to sudo without a password. | |||
sudo groupadd pcap | |||
sudo usermod -a -G pcap $USER | |||
sudo chgrp pcap /usr/sbin/tcpdump | |||
sudo setcap cap_net_raw,cap_net_admin=eip /usr/sbin/tcpdump | |||
sudo ln -s /usr/sbin/tcpdump /usr/bin/tcpdump | |||
</source> | |||
Revision as of 19:25, 12 August 2019
There are various ways to tap a Wireshark to a linux instance in order to observe live communication. Here below I am utilising named-pipes where tcpdump is redirecting its output to.
Prerequisites - Allow root SSH on Ubuntu Edit /etc/ssh/sshd_config to allow root password logins through ssh. As shown below, comment out #PermitRootLogin without-password and add PermitRootLogin yes.
# Authentication: LoginGraceTime 120 #PermitRootLogin without-password PermitRootLogin yes
Create named pipe on a system A where Wireshark is installed
sudo mkfifo /tmp/remote
Read from the pipe on system A to Wireshark
sudo wireshark -k -i /tmp/remote
Connect to system B as root user to a remote node then redirect tcpdump output to the named pipe over ssh to system A
ssh root@monior-this-host.com "tcpdump -s 0 -U -n -w - -i eth0 not port 22" > /tmp/remote
Filters
Operators
! - no, && - and, || - or
No STP, No Arp, No ipv6, no nbns, no DHCP
!stp && !arp && !ipv6 && !dhcpv6 && !nbns && !bootp.option.type == 53
Allow non-root (current) user to run tcpdump
#!/usr/bin/env bash # NOTE: This will let anyone who belongs to the 'pcap' group # execute 'tcpdump' # NOTE2: User running the script MUST be a sudoer. It is # convenient to be able to sudo without a password. sudo groupadd pcap sudo usermod -a -G pcap $USER sudo chgrp pcap /usr/sbin/tcpdump sudo setcap cap_net_raw,cap_net_admin=eip /usr/sbin/tcpdump sudo ln -s /usr/sbin/tcpdump /usr/bin/tcpdump