SSO - Single Sign On
Jump to navigation
Jump to search
The printable version is no longer supported and may have rendering errors. Please update your browser bookmarks and please use the default browser print function instead.
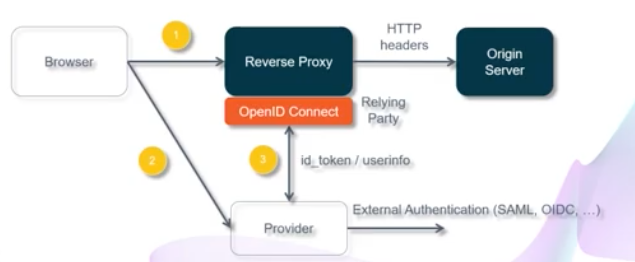
SSO (Reverse Proxy) Architecture
Browser goes to URL(1), via rev-proxy gets redirected to IdP(2)
Example implementations:
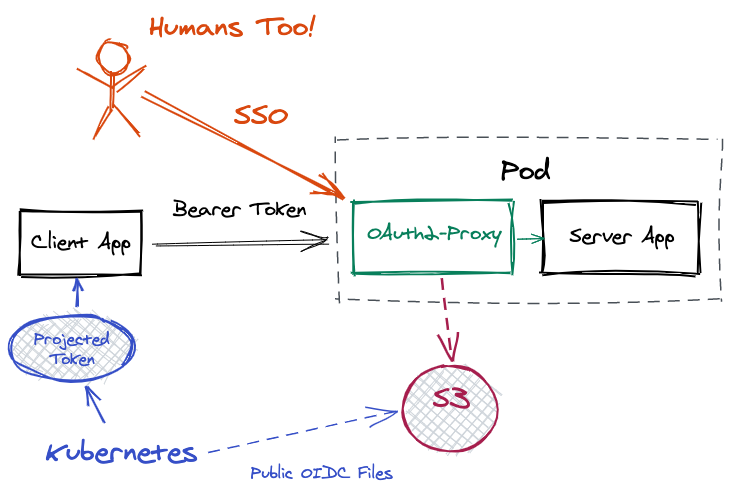
oauth2-proxy reverse proxy
oidc-issuer-urlmust match the issuer (iss) claim in your tokens. This is where you are hosting the public OIDC discovery documents you configured.client-idneeds to match the audience (aud) claim in your tokens. You set the audience in the Pod spec in the projected volume details.cookie-secretand client-secret don’t matter for machine users. But they have to be set for OAuth2-Proxy to start up. Just set them with junk data.skip-jwt-bearer-tokensis what allows OAuth2-Proxy to verify ID Tokens in a bearer header directly. Otherwise it would look for a session cookie for authorization purposes.email-domainsmust be*for Kubernetes machine users support. If you glance above at the decoded contents of a projected token payload, you’ll notice there’s no email claim. Hence the * is mandatory.
Resources
- Kubernetes Hands-On Self-Paced Course OAuth+OIDC