Kubernetes/Security and RBAC
Jump to navigation
Jump to search
Role Base Access Control
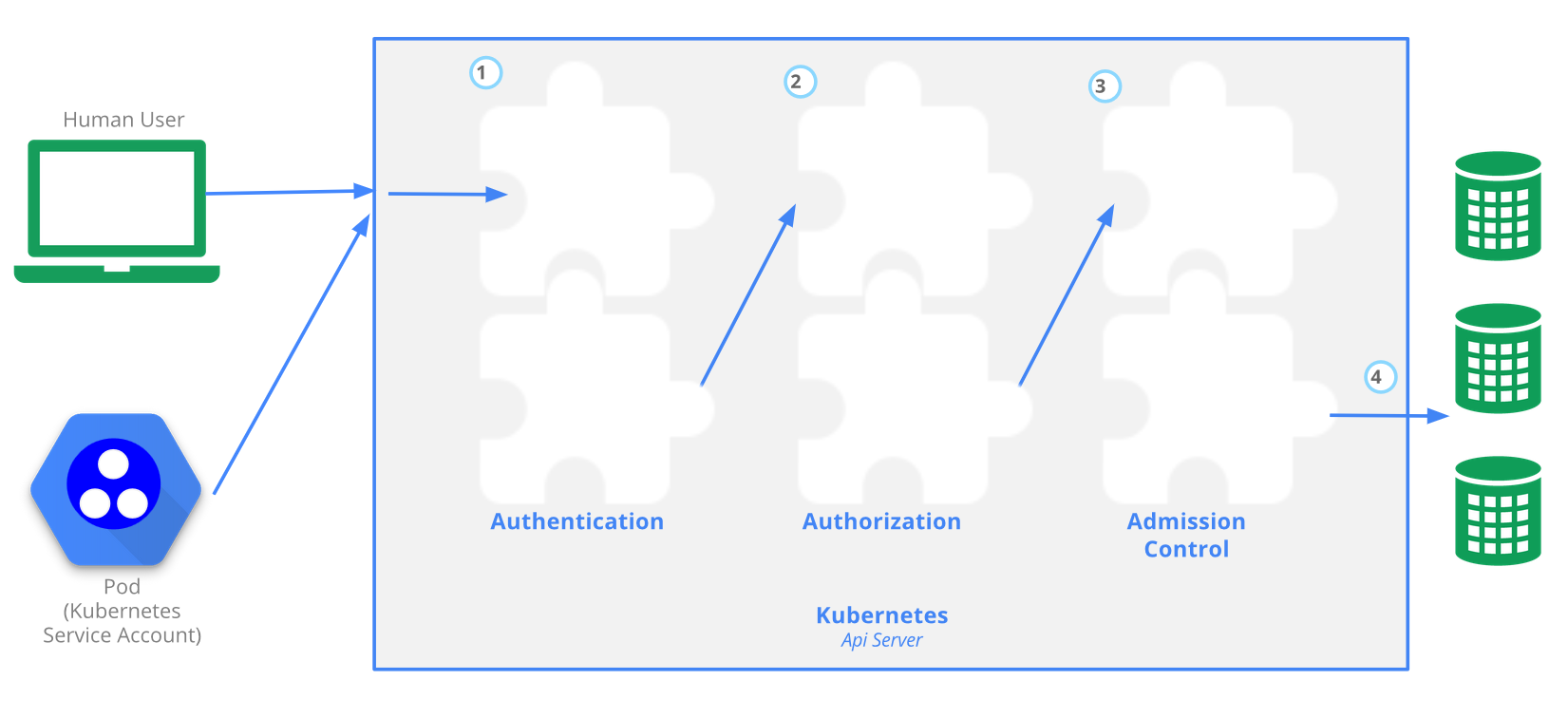
The Kubernetes API server provides CRUD (Create, Read, Update, Delete) interface for interacting with cluster state over a RESTful API. API calls can come only from 2 sources:
- kubectl
- POD
There is 4 stage process
- Authentication
- Authorization
- Admission
- Writing configuration CRUD actions to etcd database
At the admission stage RBAC access is evaluated. RBAC it self has 4 resources, divided over 2 groups
| Group-1 namespace resources | Group-2 cluster level resources | resources type |
|---|---|---|
| roles | cluster roles | defines what can be done |
| role bindings | cluster role bindings | defines who can do it |