Cryptography
Jump to navigation
Jump to search
Encryption protocols
| Symmetric | Asymmetric |
|---|---|
|
|
. System-1 System-2
#Encryption decryption
download
[data encrypted] -----> [data decrypted]
- with public2 key - with private2 key
#Signing
[data encrypted] -----> [data decrypted]
- with public2 key - with private2 key
- signed with private1 key - verified signature with public1 key
#Note, where needed the public key exchange happen, eg. via CA distribution process or protocol initialisation etc.
- Signing
- if you sign anything with private key, the only way to verify the signature is to decrypt with the matching public key.
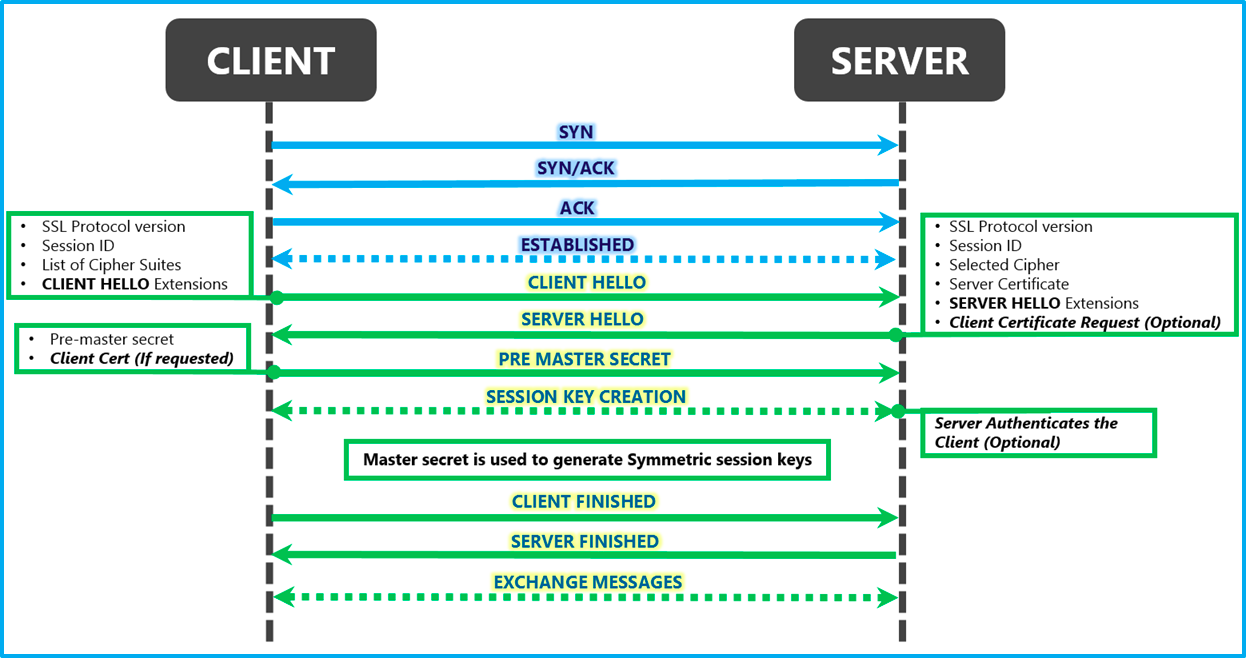
SSL and TLS
- SSL - Secure Socket Layer, proprietary by Netscape
- TLS - Transport Layer Security, open-standard, based on SSL created by IETF (Internet Engineering Task Force)
Communication via SSL FTP,SMTP, HTTP operate at Application Layer, but when we securing with SSL (SSL wrapper) we put cryptographic wrapper around the communication at the Transport Layer
.HTTP,FTP,SMTP.----- 7.Application
| | 6.Presentation
| | 5.Session
\SSL Wrapper/ ----- 4.Transport
3.Network
2.Data Link
1.Physical
SSL hybrid communication
- Asymmetric Key Exchange
- system-1 sends its Public key (Public Key Exchange) to system-2
- system-1 generates session Symmetric key, then encrypts with Private key and sends to system-2
- system-2 decrypts the Symmetric key with public keys of system-1
- Symmetric Data Exchange session starts
TLS Handshake or Public Key Exchange (PKE)