Cisco swithport security
Jump to navigation
Jump to search
Yeah, this is for a reference only not a tutorial so please do not be too critical. The output is from Cisco Packet Tracer 6.1.
Configure
interface FastEthernet0/1 switchport mode access !required otherwise you'll get an error message: Command rejected: FastEthernet0/1 is a dynamic port switchport port-security !enables port-security feature, if not applied the port security status will be disabled and sticky mac addresses can't be learnt switchport port-security maximum 2 !maximum mac addresses allowed switchport port-security mac-address sticky !enables sticky mac addresses learning switchport port-security violation restrict !sets violation policy to restrict, switchport port-security mac-address sticky 00E0.B027.2245 !auto-created - saves learnt mac address to configuration file
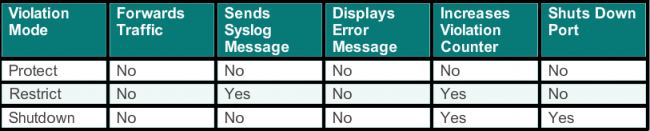
Security Violation Modes
- Protect - when a number MAC addresses reaches allowed number, packets from other ports are dropped, there is no notification
- Restrict - same as Protect policy but there is notification that a security violation has occured
- Shutdown (default) - shutdowns port, sets into error-disabed state
Note! Shutdown policy as other sources mention also sends an SNMP trap and logs a syslog message. This is different to the table form CCNAv5 course.
Verify
S1#show port-security interface fa0/1 Port Security : Enabled #because of switchport port-security command applied Port Status : Secure-up #indicates port-security status, if Secure-shutdown port is in error-disabled state Violation Mode : Restrict #because of switchport port-security violation restrict, shutdown is default Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 2 #because of switchport port-security maximum 2 command Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 1 Last Source Address:Vlan : 00E0.B027.2245:1 Security Violation Count : 0
S1#show port-security
Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action
(Count) (Count) (Count)
--------------------------------------------------------------------
Fa0/1 2 1 0 Restrict
Fa0/2 2 1 0 Shutdown
----------------------------------------------------------------------
S1#show port-security address Secure Mac Address Table ------------------------------------------------------------------------------- Vlan Mac Address Type Ports Remaining Age (mins) ---- ----------- ---- ----- ------------- 1 00E0.B027.2245 SecureSticky FastEthernet0/1 - 1 0001.647C.697E SecureSticky FastEthernet0/2 - ------------------------------------------------------------------------------ Total Addresses in System (excluding one mac per port) : 0 Max Addresses limit in System (excluding one mac per port) : 1024
S1#show int fastEthernet 0/1 switchport Name: Fa0/1 Switchport: Enabled Administrative Mode: static access #because of switchport mode access command, by a default it is set to 'dynamic auto' Operational Mode: static access Administrative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: native Negotiation of Trunking: Off Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk private VLANs: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none
Troubleshooting
At first we should verify if an interface is in err-disable mode
show interface fa0/1 status