Difference between revisions of "AWS"
Jump to navigation
Jump to search
| Line 2: | Line 2: | ||
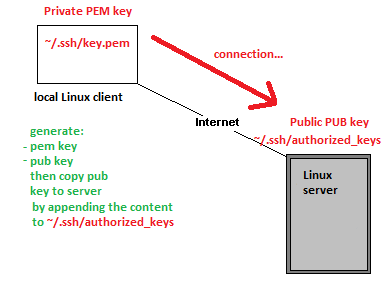
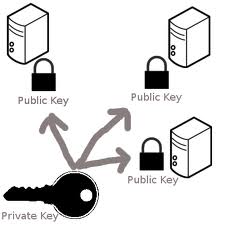
SSH theory using a private and public key | SSH theory using a private and public key | ||
<gallery widths=400px heights=300px> | <gallery widths=400px heights=300px> | ||
File:Ssh-pem-pub-keys.png | File:Ssh-pem-pub-keys.png | ||
File:Private-public-key.jpg | File:Private-public-key.jpg | ||
</gallery> | </gallery> | ||
Change permissions of the key to ready only by owner as per [http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/EC2_GetStarted.html#EC2_ConnectToInstance_Linux Getting Started with Amazon EC2 Linux Instances] | Change permissions of the key to ready only by owner as per [http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/EC2_GetStarted.html#EC2_ConnectToInstance_Linux Getting Started with Amazon EC2 Linux Instances] | ||
Revision as of 12:28, 18 August 2013
ssh to EC2 instance
SSH theory using a private and public key
Change permissions of the key to ready only by owner as per Getting Started with Amazon EC2 Linux Instances
chmod 400 mykey.pem -r------- 1 user user 1766 Aug 18 01:17 mykey.pem
- Ubuntu user: ubuntu (confirmed)
- RedHat user: root (tbc)
- Amazon branded instances: ec2-user (to be confirm)
Connecting and useful flags -l username specifies linux account user name, -v verbose mode
ssh -i mykey.pem ubuntu@ec2-user@ec2-99-99-99-99.compute-1.amazonaws.com
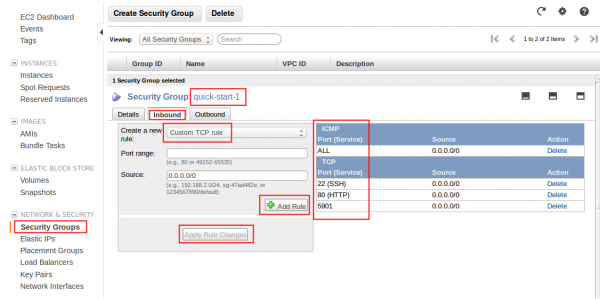
EC2 Security Group
Remember to assing the security group that applies to your scheme on your instance. Having port open on the instance does not mean you will be able to access from outside. It must bypass EC2 Security Group first. Overview below: