Ssh tunnel - SOCKS proxy
Dynamic port forwarding
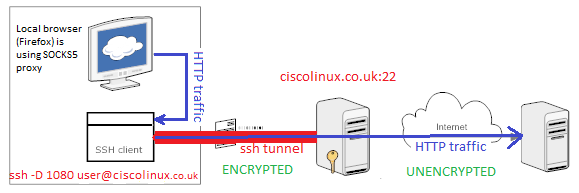
Tunnelling over our Internet link it sounds already exiting, isn't it?. But how difficult is it? Do we need any complex and sophisticated configuration of hardware and software? Hmm.. it is not necessary even to involve ipsec or ssl stack to create VPN. SOCKS is built in to OpenSSH so it's trivial to run SOCKS proxy server with ssh client running with option -D. This option configures SSH client to listen on your local Linux box on specified by us tcp port. Then we will use SOCKS5 proxy configuration built into most of Internet browsers to connect to.
First, SSh to your localhost server with -D {port_number}option. It creates ssh tunnel listening on your local host TCP port_number
ssh -D 1080 username@your.server.com -N will disable remote shell, Ctrl+C to kill the connection
The above command sets up a SOCKS proxy server supporting SOCKS4 and SOCKS5 protocols leveraging dynamic application-level port forwarding through the ssh tunnel.
- Options explained
ssh -D [bind_address:]portspecifies a local dynamic application-level port forwarding. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address. Whenever a connection is made to this port, the connection is forwarded over the secure channel, and the application protocol is then used to determine where to connect to from the remote machine. Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKS server. Only root can forward privileged ports. Dynamic port forwardings can also be specified in the configuration file.
Firefox
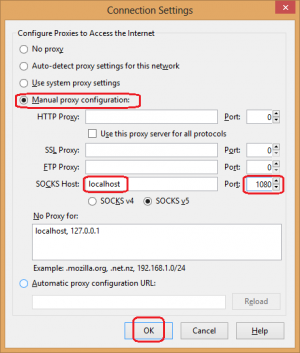
Open Firefox > Options > Advanced > Network tab > Connection Settings... > Manual procy configuration > SOCKS Host: localhost Port: 1080 > OK
Since now on you are using @your.server.com geo locations, what you can check at http://whatismyipaddress.com/ . It works with Amazon EC2 instances.
Chromium
Open Chrome from a terminal passing following arguments
chromium-browser --proxy-server="socks5://127.0.0.1:1080"