Difference between revisions of "Azure/az-cli"
| Line 127: | Line 127: | ||
</source> | </source> | ||
= List of SQL servers = | == List of SQL servers == | ||
<source lang="bash"> | <source lang="bash"> | ||
# List of Ms.SQL servers | # List of Ms.SQL servers | ||
Revision as of 11:27, 17 July 2020
Azure tools
- az - Azure CLI
- Powershell AZModule eg. to copy files - requires PS 5.1+
- blob storage .msi
- Powershell DSC Desired State Configuration system
- VMagent custom script extension - runs on Azure VMs, allows to run one-off scripts
az - Azure CLI
# Linux curl -L https://aka.ms/InstallAzureCli | bash #Windows - download and install msi PS C:> wget https://aka.ms/installazurecliwindows PS C:> wget https://azurecliprod.blob.core.windows.net/msi/azure-cli-2.0.63.msi
Login and basic commands
PS C:> az login PS C:> az account show --output table EnvironmentName IsDefault Name State TenantId ----------------- ----------- --------------------------- ------- ------------------------------------ AzureCloud True Microsoft Azure Sponsorship Enabled aaaaaaaa-bbbb-4a1a-9b26-bac3cb7dcccc
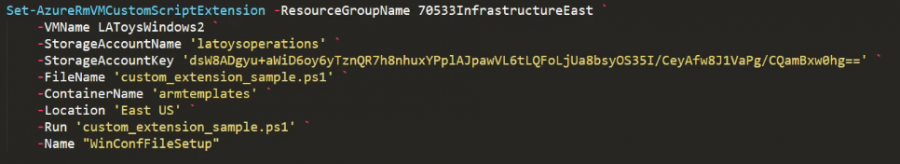
VMagent custom script extension
Windows
$fileUri = @("https://xxxxxxx.blob.core.windows.net/buildServer1/1_Add_Tools.ps1",
"https://xxxxxxx.blob.core.windows.net/buildServer1/2_Add_Features.ps1",
"https://xxxxxxx.blob.core.windows.net/buildServer1/3_CompleteInstall.ps1")
$Settings = @{"fileUris" = $fileUri};
$storageaccname = "xxxxxxx"
$storagekey = "1234ABCD"
$ProtectedSettings = @{"storageAccountName" = $storageaccname; "storageAccountKey" = $storagekey; "commandToExecute" = "powershell -ExecutionPolicy Unrestricted -File 1_Add_Tools.ps1"};
#run command
Set-AzureRmVMExtension -ResourceGroupName myRG `
-Location myLocation `
-VMName myVM `
-Name "buildserver1" `
-Publisher "Microsoft.Compute" `
-ExtensionType "CustomScriptExtension" `
-TypeHandlerVersion "1.9" `
-Settings $Settings `
-ProtectedSettings $ProtectedSettings
Linux
az vm extension set \ --resource-group myResourceGroup \ --vm-name myVM --name customScript \ --publisher Microsoft.Azure.Extensions \ --settings ./script-config.json
Resources
Access and login methods
Azure Service Principal
You can give an application access to Azure Stack resources by creating a service principal that uses Azure Resource Manager. A service principal lets you delegate specific permissions using role-based access control. Steps
- Register an app with Azure AD
- Create identity for the app, this identity is called Service Principle (SP)
- Alternatively you can use Managed Service Identity (MSI)
Eg. If AKS needs to pull an image from ACR it needs permissions to do so. The Service Principal controls the access.
Az PowerShell module
Note az replaced AzureRM that is backwards compatible but both shouldn't be installed at the same time. Official installation guide might come here very handy. Otherwise follow quick steps:
Install Az module and login to Azure cloud
<syntaxhighlightjs lang="PowerShell">
- Verify
C:\> $PSVersionTable.PSVersion #check required version PowerShell 5.x or 6.x C:\> Get-InstalledModule -Name Az -AllVersions | select Name,Version Name Version
-------
Az 4.4.0
- Install and import
C:\> Install-Module -Name Az -AllowClobber # admin rights required C:\> Import-Module Az # Import the module into the PowerShell session C:\> Get-Command *az* # List all available PShell commands
- Login
C:\> Connect-AzAccount # Connect to Azure with a browser sign in token WARNING: To sign in, use a web browser to open the page https://microsoft.com/devicelogin and enter the code DAAAAAAAA to authenticate.
Account : john@example.com SubscriptionName : Microsoft Azure Sponsorship SubscriptionId : aaaaaaaa-bbbb-cccc-dddd-eeeeeeeeeeee TenantId : bbbbbbbb-cccc-dddd-eeee-ffffffffffff Environment : AzureCloud
- Update module
C:\> Update-Module -Name Az </syntaxhighlightjs>
az cli - usage
List of Vnets
$ az network vnet list -o table # List of VNETs within resource group $ az network vnet list --resource-group infra_rg -o tsv | cut -f9
List of all subnets
#!/bin/bash
for ResourceGroup in $(az group list -o tsv | cut -f4); do
for VNET in $(az network vnet list --resource-group $ResourceGroup -o tsv | cut -f9); do
echo "### ResourceGroup: $ResourceGroup VNET: $VNET"
az network vnet subnet list --resource-group $ResourceGroup --vnet-name $VNET -o tsv | cut -f1,9,13 | column -t
done
done
List of SQL servers
# List of Ms.SQL servers
az sql server list --resource-group infra-euw1 -o tsv | cut -f1,6-10,12-13
# List all database servers
for AzureResourceGroup in $(az group list -o tsv | cut -f4); do
echo "### $VNET ResourceGroup: $AzureResourceGroup"
az sql server list --resource-group $AzureResourceGroup -o tsv | cut -f1,6-10,12-13
done
#List all databases
for AzureResourceGroup in $(az group list -o tsv | cut -f4); do
for DbServer in $(az sql server list --resource-group $AzureResourceGroup -o tsv | cut -f1,6-10,12-13); do
echo "### Dbserver: $DbServer, ResourceGroup: $AzureResourceGroup"
az sql db list --resource-group $AzureResourceGroup --server $DbServer
done
done
az resource list -o table --query "[?type=='Microsoft.DBforMySQL/servers'].{name:name, group:resourceGroup}"
az resource list -o table | grep 'Microsoft.DBforMySQL/servers'
az resource list -o table | grep -i 'sql' | sort -k4
List of Virtual Gateways
# List all vpn virtual gateways
for AzureResourceGroup in $(az group list -o tsv | cut -f4); do
echo "### $VNET ResourceGroup: $AzureResourceGroup"
az network vnet-gateway list -g $AzureResourceGroup -o table | grep -ve '---'
done
List scale sets
### VMScaleSets
# List VMSS
az vmss list --resource-group client1 -o table
Name ResourceGroup Location Zones Capacity Overprovision UpgradePolicy
----------------------- --------------- ---------- ------- ---------- --------------- ---------------
client1_external_vmss client1 westeurope 1 2 3 2 True Manual
client1_internal_vmss client1 westeurope 1 2 3 1 True Manual
client1_worker_vmss client1 westeurope 1 2 3 1 True Manual
# List VMSS instances
az vmss list-instances --resource-group client1 --name client1_external_vmss -o table
az vmss nic list -g client1 --vmss-name client1_external_vmss --query [].{ip:ipConfigurations[0].privateIpAddress} -o tsv
# Get VMs ip addresses in VMSS sets
$ cat > list-all-vmss-ips.sh <<'EOF'
#!/bin/bash
for AzureResourceGroup in $(az group list -o tsv | cut -f4)
do
for vmss in $(az vmss list --resource-group $AzureResourceGroup -o tsv | cut -f4)
do
echo "### $VNET ResourceGroup: $AzureResourceGroup ScaleSet: $vmss"
az vmss nic list -g $AzureResourceGroup --vmss-name $vmss --query [].{ip:ipConfigurations[0].privateIpAddress} -o tsv
done
done
EOF