Difference between revisions of "OpenSSH/Tunelling"
| Line 6: | Line 6: | ||
= Local port forwarding - straight tunnel = | = Local port forwarding - straight tunnel = | ||
Used when only '''gateway/bastion''' can talk directly to databases (or other servers). The connection is made through gateway so the database see connection coming from the gateway and allows it. | |||
-L <<span style="color: green">local-port-to-listen</span>>:<<span style="color: blue">remote-host</span>>:<<span style="color: blue">remote-port</span>> <gateway> | -L <<span style="color: green">local-port-to-listen</span>>:<<span style="color: blue">remote-host</span>>:<<span style="color: blue">remote-port</span>> <gateway> | ||
Example | Example | ||
in- | in-front-of-firewall@localhost:$ ssh -f -N -T -L<span style="color: green">8080</span>:<span style="color: blue">remotehost.com:8888</span> jumpbox.com | ||
Example of connecting to Azure MySQL | |||
<source lang=bash> | |||
# Create a tunnel, localhost will be listening on port 3306 | |||
ssh -fNT -L3306:database-eu.mysql.database.azure.com:3306 db@bastion | |||
# Connect, to localhost, by default that port 3306, will forward connection over | |||
# the tunnel to database database-eu.mysql.database.azure.com:3306 using username 'admin@database-eu' | |||
mysql -h 127.0.0.1 -u admin@database-eu -p | |||
</source> | |||
= Remote port forwarding (reverse SSH tunnel) = | = Remote port forwarding (reverse SSH tunnel) = | ||
Revision as of 19:04, 22 January 2019
Different types of tunnelling:
- Local port forwarding: connections from the SSH client are forwarded via the SSH server, then to a destination server
- Remote port forwarding (reverse SSH tunnel): connections from the SSH server are forwarded via the SSH client, then to a destination server
- Dynamic port forwarding: connections from various programs are forwarded via the SSH client, then via the SSH server, and finally to several destination servers
Local port forwarding - straight tunnel
Used when only gateway/bastion can talk directly to databases (or other servers). The connection is made through gateway so the database see connection coming from the gateway and allows it.
-L <local-port-to-listen>:<remote-host>:<remote-port> <gateway>
Example
in-front-of-firewall@localhost:$ ssh -f -N -T -L8080:remotehost.com:8888 jumpbox.com
Example of connecting to Azure MySQL
# Create a tunnel, localhost will be listening on port 3306 ssh -fNT -L3306:database-eu.mysql.database.azure.com:3306 db@bastion # Connect, to localhost, by default that port 3306, will forward connection over # the tunnel to database database-eu.mysql.database.azure.com:3306 using username 'admin@database-eu' mysql -h 127.0.0.1 -u admin@database-eu -p
Remote port forwarding (reverse SSH tunnel)
-R <sourcePort>:<forwardToHost>:<onPort> <gate>
// //
in-front-of-firewall@server1 //NAT// behind-firewall@server2
<-------------------------------------------
2. the tunnel listens on // FW// 1. this server initiates a -R reverse tunnel (because is allowed out through FW/NAT)
localhost:2222 port and // //
any data forwards down through the tunnel to port 22 of the other end of the tunnel
--------------------------------------------
>>> :2222 >>>>> tunnel >>>>> :22
--------------------------------------------
From the firewalled host:
behind-firewall@server2:$ ssh -f -N -T -R2222:localhost:22 in-front-of-firewall@server1.com
This tells your client to establish a tunnel with a -Remote entry point. Anything that attaches to port 2222 on the far end of the tunnel will actually reach "localhost port 22" (computer that you execute the command).
Then on the in-front-of-firewall@server1 you can connect over ssh to localhost:2222 will send all traffic through the tunnel to behind-firewall@server2
ssh -p 2222 behind-firewall@localhost
This resolves issue for a remote users that needs a temporary access from theirs machines that are in-front-of-firewall.
The other options are:
-ftells ssh to background itself after it authenticates, so you don't have to sit around running something on the remote server for the tunnel to remain alive.-Nsays that you want an SSH connection, but you don't actually want to run any remote commands. If all you're creating is a tunnel, then including this option saves resources.-Tdisables pseudo-tty allocation, which is appropriate because you're not trying to create an interactive shell.
Local and Remote port forwarding graphs
Local port forwarding
Remote port forwarding
Show current tunnels
Shows -L local forwarding tunnels
netstat -tpln | grep ssh #t: TCP, p: show process, l: listening, n: numeric values (header added, tested on Debian wheezy) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:1443 0.0.0.0:* LISTEN 4036/ssh
Which can be read as: SSH (not SSHd) is listening to local TCP port 1443
if you only want to list tunnels created by ssh
$ sudo lsof -i -n | egrep '\<ssh\>' ssh 19749 user 3u IPv4 148088244 TCP x.x.x.x:39689->y.y.y.y:22 (ESTABLISHED) ssh 19749 user 4u IPv6 148088282 TCP [::1]:9090 (LISTEN) ssh 19749 user 5u IPv4 148088283 TCP 127.0.0.1:9090 (LISTEN)
(that would be a -L 9090:localhost:80 tunnel)
Shows -R reverse tunnels
if you want to see the tunnels / connections made to a sshd:
$ sudo lsof -i -n | egrep '\<sshd\>' sshd 15767 root 3u IPv4 147401205 TCP x.x.x.x:22->y.y.y.y:27479 (ESTABLISHED) sshd 15842 user 3u IPv4 147401205 TCP x.x.x.x:22->y.y.y.y:27479 (ESTABLISHED) sshd 15842 user 9u IPv4 148002889 TCP 127.0.0.1:33999->127.0.0.1:www (ESTABLISHED) sshd 1396 user 9u IPv4 148056581 TCP 127.0.0.1:5000 (LISTEN) sshd 25936 root 3u IPv4 143971728 TCP *:22 (LISTEN)
the ssh-daemon listens on port 22 (last line), 2 subprocesses are spawned (first 2 lines, login of 'user'), a -R tunnel created on port 5000, and a -L tunnel which forwards a port from my (local) machine to localhost:80 (www).
sudo lsof -i -n | egrep '\<sshd\>' | grep -v ":ssh" | grep LISTEN | sed 1~2d | awk '{ print $2}' | while read line; do sudo lsof -i -n | egrep $line | sed 3~3d | sed 's/.*->//' | sed 's/:......*(ESTABLISHED)//' | sed 's/.*://' | sed 's/(.*//' | sed 'N;s/\n/:/' 2>&1 ;done
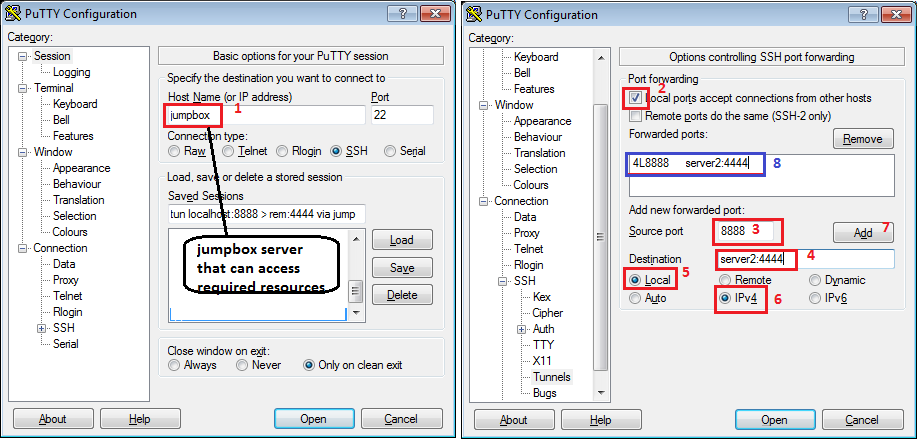
Windows Putty ssh tunnelling
The all above can also be achieved using Putty.
Putty Local port forwarding tunnel
Once connected the tunnel is established and from the local PC you can eg. go http://127.0.0.1:8888 that in effect pull data from server2:4444. If you don't want to have open CLI session you can disable Pseudo TTY terminal in Putty>Connection>SSH>TTY, tick Don't allocate a pseudo-terminal
References
- The Black Magic Of SSH vimeo
- ssh-tunneling-work unix.stackexchange.com, diagrams
- ssh tunnels 21 usages of openssh